Free Sharing Of Citrix 1Y0-202 Brain Dumps From Lead2pass:
https://www.lead2pass.com/1y0-202.html
QUESTION 51
Scenario: Users of the Finance group lost access to their local drive through their desktop-hosted applications. Due to this issue, those users missed a critical deadline. Now management has requested that a Citrix Administrator provide a report of recent changes to the environment.
Which tool could the administrator use to generate a report of recent changes to the environment?
A. Event logs
B. StoreFront
C. Citrix Studio
D. Citrix Director

Answer: C
QUESTION 52
Scenario: A Citrix Administrator needs to audit logins from the NetScaler Gateway. Company policy states that the logs need to be sent to a centralized server.
What should the administrator configure to audit ICA sessions on the NetScaler Gateway?
A. SYSLOG
B. HDX Monitoring
C. Application Firewall
D. Configuration Logging
E. NetScaler Web Logging
Answer: A
QUESTION 53
A Citrix Administrator has received several reports of network connectivity issues throughout the day and thinks these issues might be affecting the vDisk assigned to Desktop OS machines.
What should the administrator monitor to determine if the network issues have affected disk streaming?
A. NetStat Utility
B. Error messages in Citrix Studio
C. The number of warning messages in Citrix Director
D. The number of retries performed by the Streaming service
Answer: D
QUESTION 54
A Citrix Administrator monitoring virtual machine network performance is unable to see memory utilization data in XenCenter.
Why is the administrator unable to monitor memory utilization data?
A. SR-IOV is NOT configured.
B. Performance monitor service is NOT running.
C. XenServer tools are NOT installed on the virtual machines.
D. Additional administrative rights are required to monitor memory utilization.
Answer: C
QUESTION 55
Scenario: A Citrix Administrator created a new Delivery Group named ‘Sales’ and assigned Desktop OS machines to users who are members of the Delivery Group. The Server OS machines assigned to the Delivery Group are based on Windows Server 2012 R2.
Where should the administrator look to identify the number of active sessions to Server OS machines assigned to the ‘Sales’ Delivery Group?
A. Filter in Citrix Studio
B. Event Log on the StoreFront server
C. Event Log on the Delivery Controller server
D. Filter by collection in the Provisioning Services Console
Answer: A
QUESTION 56
Scenario: When a Citrix Administrator attempts to shadow a user connected to a Desktop OS machine, the following error is displayed:
Failed to initiate Remote Assistance
What could be the cause of this issue?
A. Remote Assistance is NOT enabled on the host machine.
B. The administrator created a firewall exception for port 3398.
C. The administrator added Citrix Director to the Intranet Zone trusted sites.
D. The administrator does NOT have the proper scope for the user’s Desktop OS machine.
Answer: A
QUESTION 57
A Citrix Administrator needs to obtain logs from Machine Creation Services.
Which .config file should the administrator manually modify to enable logging?
A. BrokerService.exe.Config
B. Citrix.Configuration.SdkWcfEndpoint.exe.Config
C. Citrix.MachineIdentity.SdkWcfEndpoint.exe.Config
D. Citrix.MachineCreation.SdkWcfEndpoint.exe.Config
Answer: D
QUESTION 58
Scenario: A Citrix Administrator created a Device Collection and a Delivery Group for the Human Resources (HR) and Accounting user groups. The administrator used the XenDesktop Setup Wizard to create the Desktop OS machines and assigned the V: drive as their personal drives. While testing all the new configurations prior to rolling out the Desktop OS machines to the HR user group, the administrator receives an error when attempting to access the V: drive. Users from the Accounting user group do NOT receive the error.
Click on the Exhibit button to view the error.
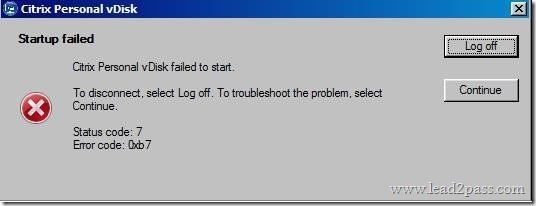
How could the administrator resolve this issue?
A. Change the V: drive to another drive letter.
B. Run the inventory update on the master image and release the image to the HR user group.
C. Recreate the master image with Personal vDisk and release that image to the HR user group.
D. Delete all of the Desktop OS machines and rerun the Streamed VM Setup Wizard to recreate the Desktop OS machines.
Answer: A
QUESTION 59
Scenario: An employee attempts to log in to a Desktop OS machine and receives the following error:
Startup Failed
Personal vDisk failed to start
Status Code: 15
How could a Citrix Administrator resolve this issue?
A. Change the startup order.
B. Restart the Desktop OS machine.
C. Run an inventory update on the Desktop OS machine.
D. Reconfigure the Virtual Delivery Agent of the affected Desktop OS machine.
Answer: C
QUESTION 60
Scenario: An application is NOT functioning as expected. The application was installed on a vDisk that has been placed in Standard mode. The vDisk is assigned to Desktop OS machines. Those Desktop OS machines have a 5 GB cache disk associated with them and the vDisk is configured to ‘cache to RAM with overflow to disk’. A Citrix Administrator attempted to view the Windows event logs from the previous week, but the logs only go back to the most recent restart.
What should the administrator do to ensure that all logs are retained?
A. Enable WINRM on the image.
B. Change the location of the write cache.
C. Use the write-eventlog PowerShell cmdlet.
D. Change the path of the event logs to that of the write cache disk.
Answer: D
1Y0-202 dumps full version (PDF&VCE): https://www.lead2pass.com/1y0-202.html
Large amount of free 1Y0-202 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDU2xnUlQ4NTdWbTQ
Maybe you also need:
1Y0-311 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDakxVRXg3aUpmTE0
